Introduction:
As a cloud and IAC consulting company. It became vital for us to meet security and compliance standards for all our client deployments. Ever since we adopted infrastructure as code to provision infrastructures to all our client environments we were looking for options to improvise our team’s code standards to ensure we match up with enterprise standards. This is when the need for static code review came and we evaluated a lot of options and finally decided to choose Checkov.
Choosing the tool:
As a cost effective cloud and infrastructure as code consulting company we cannot choose a premium priced tool which will increase our service costs to our customers. Hence, we looked for open source products as our first preference.
Checkov is actively developed and maintained by https://bridgecrew.io and supports major CI/CD tools. Checkov not only supports terraform, it supports various infrastructure as code scripts like docker,kubernetes, ansible, helm, Azure ARM, AWS Cloudformation, OpenAI etc(covers most of the services we are providing to our customers so, it turned out to be a single tool solving all our needs).
This attracted us to integrate Checkov to our IAC workflow. We use bitbucket to host our coding repositories. Since we tested it on bitbucket, I am going to write this technical blog on how to integrate checkov to perform static code analysis to terraform using bitbucket pipelines.
Prerequisites:
Since this blog only covers the DevSecOps part of terraform, this post assumes that you already have DevOps knowledge and know how to write a terraform/ansible scripts and basic understanding on bitbucket pipelines and enabled bitbucket pipeline already for the subjective repository.
We are using Gitflow workflow as our branching strategy and hence we make any new changes using a feature branch. We are also using atlantis to manage Pull requests merge changes to target repositories. Thus, we thought to run terraform code analysis on every commit to feature branch.
Implementation:
The code used in the bitbucket-pipelines.yml is below.
checkov: &checkov
step:
name: Checkov
image:
name: bridgecrew/checkov:latest
entrypoint:
- '/usr/bin/env'
- 'PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin'
script:
- checkov -d .
pipelines:
branches:
feature/*:
- <<: *checkovOnce above pipeline entry is added and pushed to the feature branch. Feature branch will check for code standards of your code.
checkov in action:
Below is the screenshot of the bitbucket pipeline failing because the terraform code is not passing all the checks made by checkov.
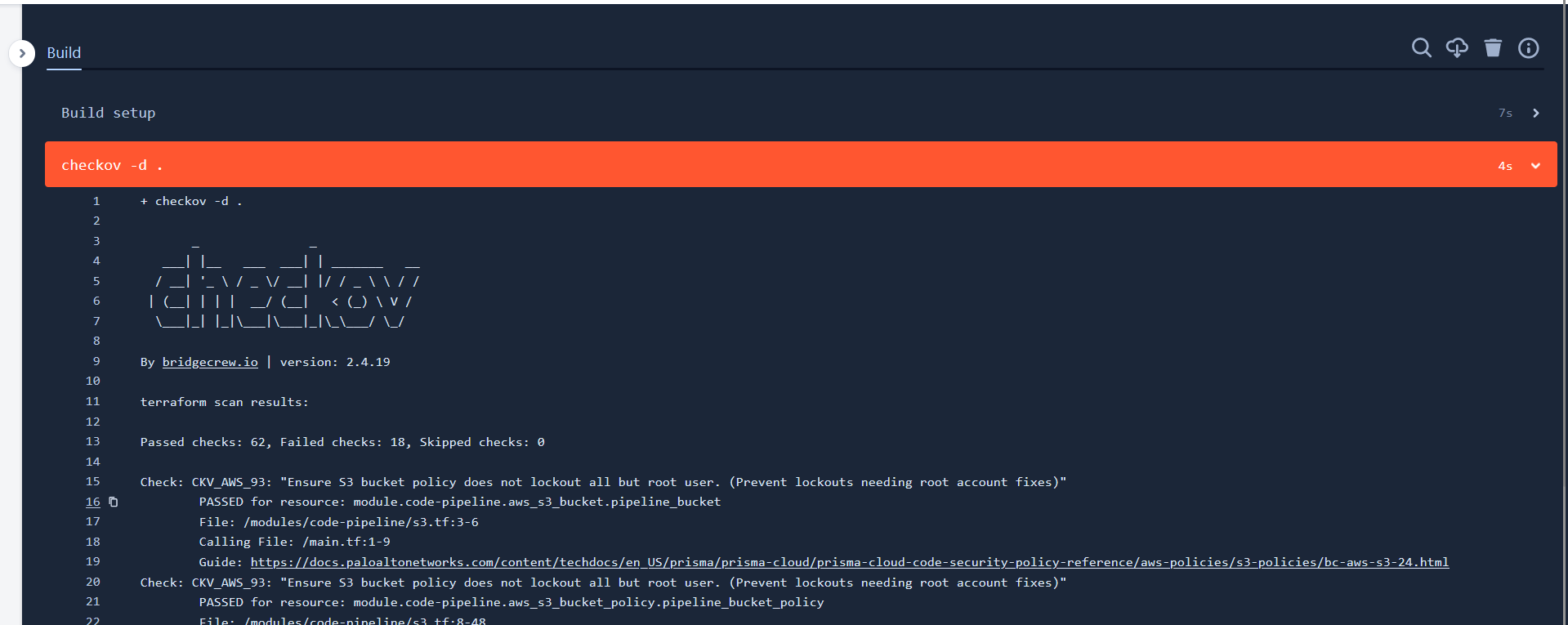
Each failed check will have a guide link explaining the issue and possible solution. Hence, it is very easy to fix the errors and pass the test.
A passed checkov checks would look like the screenshot below.
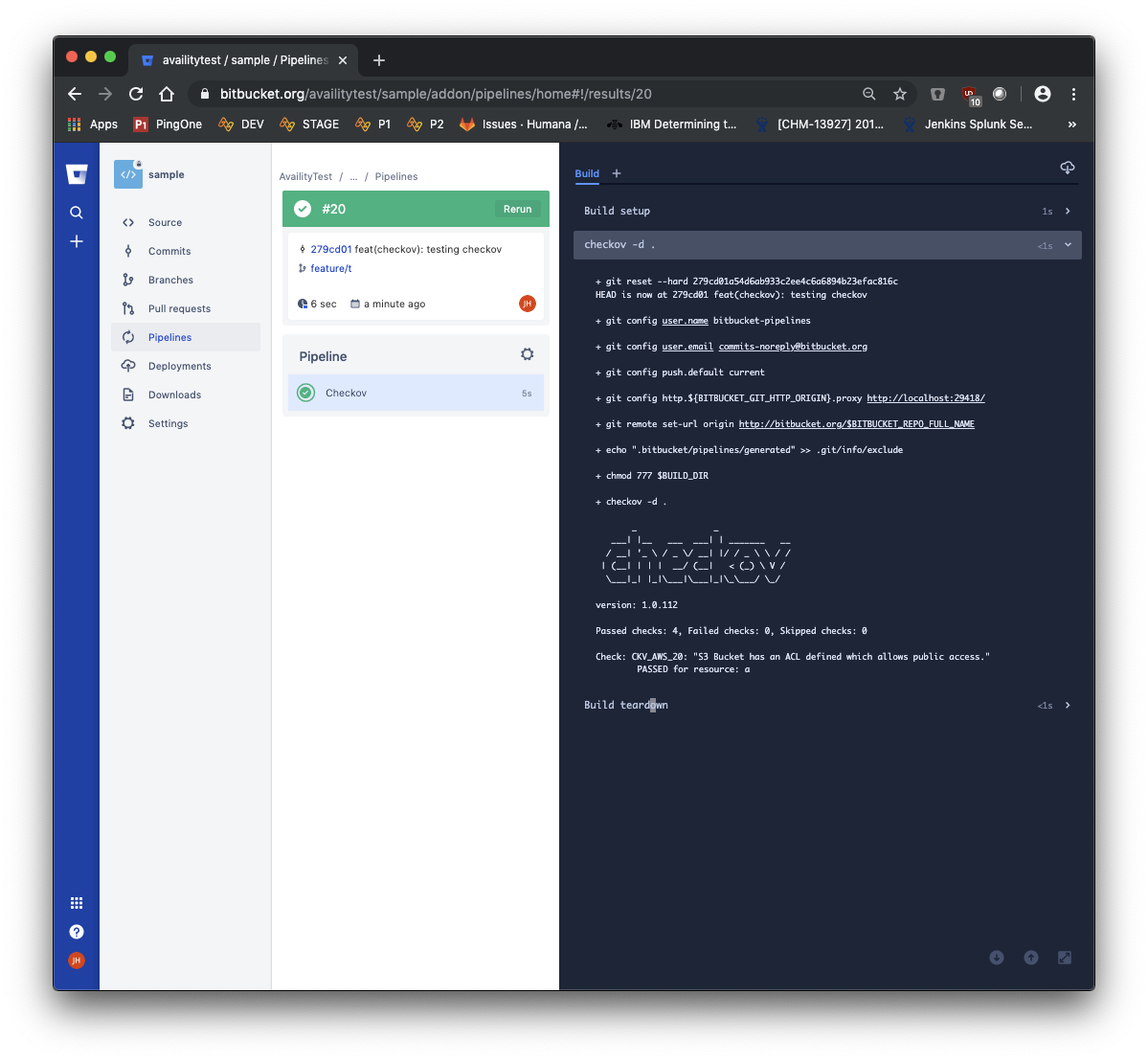
This concludes our blog post on how to implement DevSecOps to your infrastructure as code project. You can contact us if you have any requirements on DevOps, DevSecOps, IAC, Azure, AWS, GCP consulting.
FAQ
- What is the best static code analysis tool for Terraform?
Checkov is the tool that helps to check the vulnerabilities and misconfigurations of Terraform code. It is a free static code analysis tool that anyone can use it and is very easy to use
2. Can I use Bitbucket Pipeline to run Checkov for Terraform?
Yes, Since Checkov can be integrated with the Bitbucket pipeline, You can store your terraform code in the Bitbucket repository. Enable the pipeline and integrate Checkov with your pipeline to check the vulnerabilities of your terraform code.