Introduction
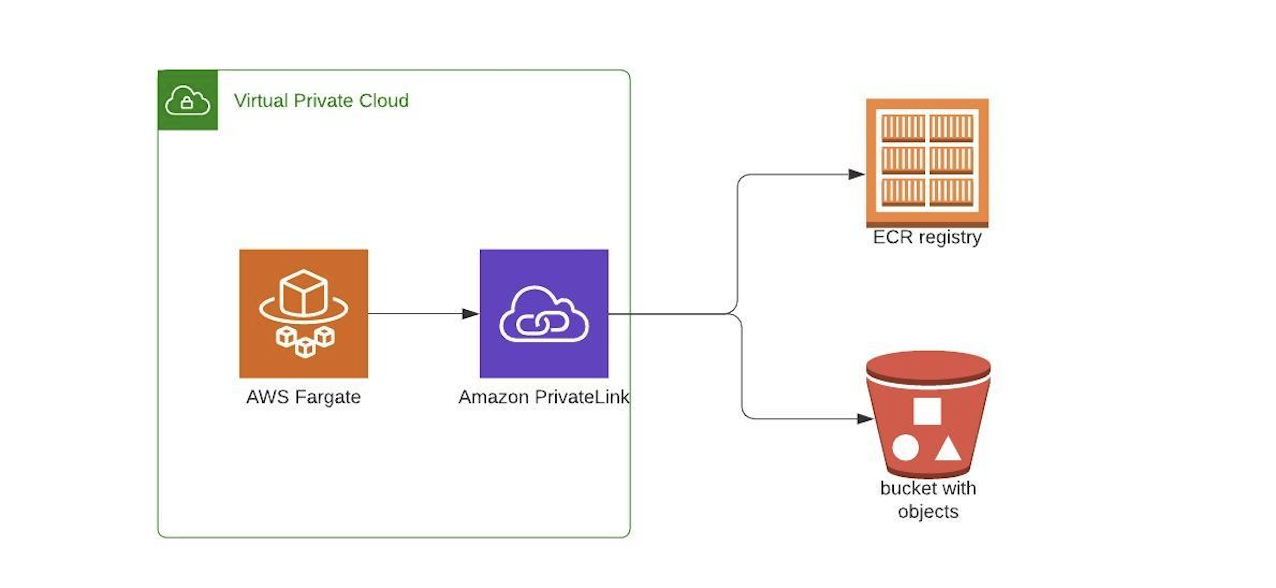
A VPC endpoint is the service providing by AWS that enables us to establish private and secure connections between your VPC and AWS services and VPC endpoint is the service powered by AWS PrivateLink. Either Internet gateway, VPN connection , NAT device, or AWS Direct Connect connection is required by VPC endpoint. Public IP is not required by instance to use the VPC endpoint service i.e Traffic between services and your VPC does not leave the Amazon network. In this blog we shall see about creating VPC endpoints for downloading images from AWS ECR to deploy containers in AWS ECS through the private link.
Reason for implementing VPC endpoint
- When we are having our custom VPC and launching resources in private subnets we need NAT gateway for those resources in private subnets to communicate with the internet.
- In such scenarios AWS charges NAT based on the amount of data that transfered via NAT.
- When you are deploying containers in private subnets you might deploy the container frequently where you need to pull the images from ECR frequently in such cases the data transferred via NAT will be more and AWS will charge you more.
- Let me give the AWS cost bar for transferring data over internet for clear understanding.
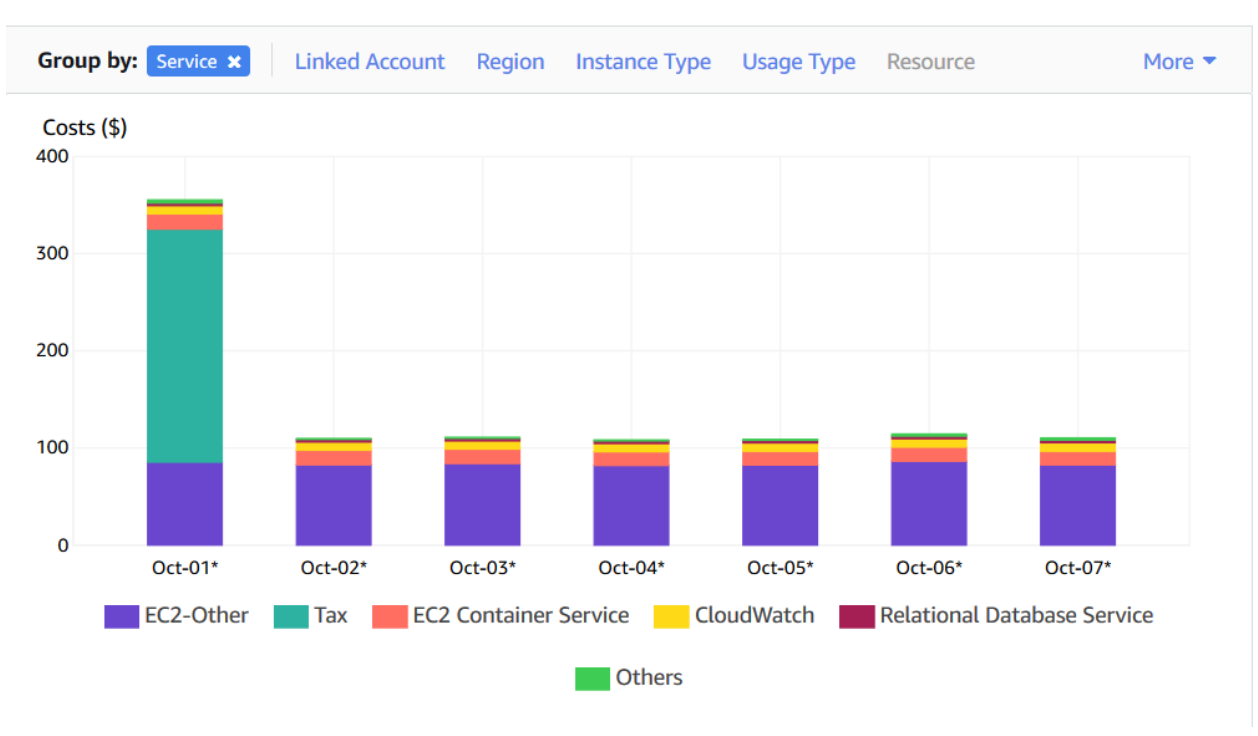
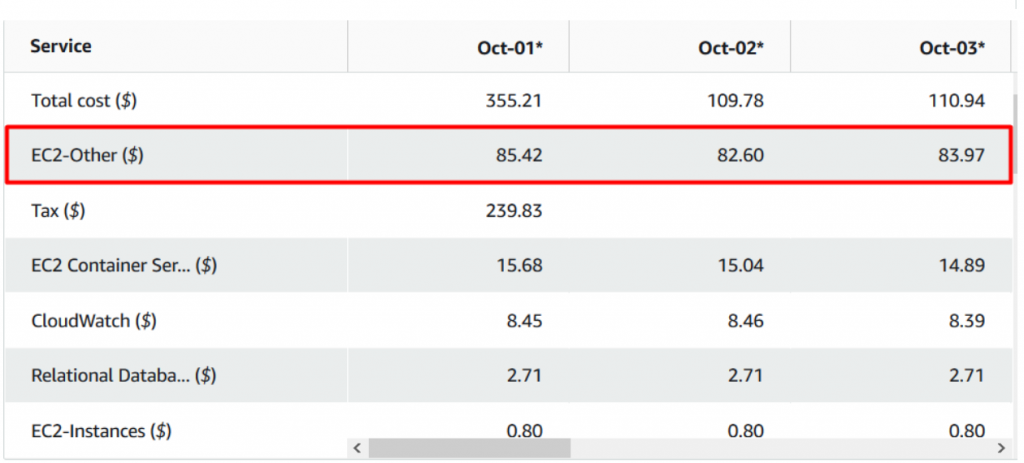
Note: Look at your EC2-other cost. Here we are pulling images for ECS over the internet.
- Once you implement VPC endpoints and the images are pulled through endpoints you can reduce the cost that you can find at the end of the blog.
- Now we shall look into how to create VPC endpoints for our resources to use private link.
Considerations for Amazon ECR VPC endpoints
Prerequisites:
- You should create ECR in your account with pre build images that are to be pulled to deploy containers.
Create the VPC endpoints for Amazon ECR
- To create VPC endpoint ECR, navigate to VPC dashboard and then click on VPC endpoint in the left panel.
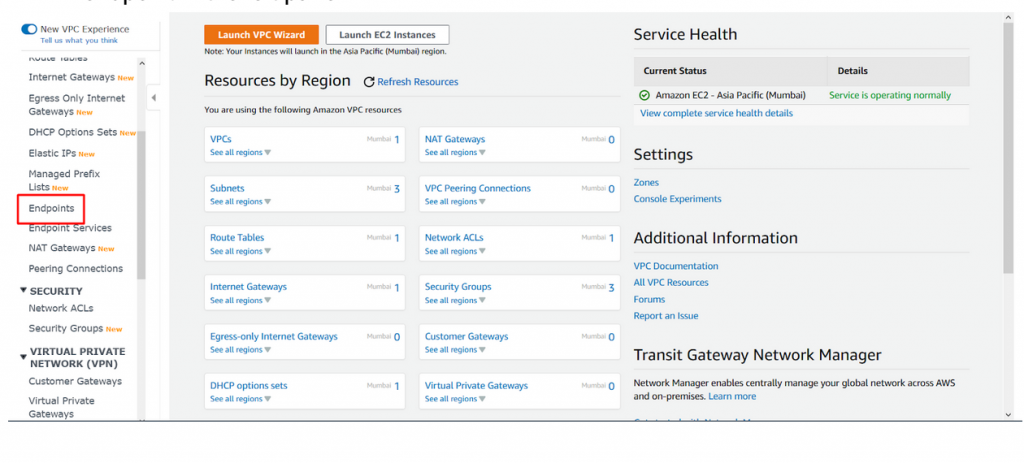
- Click on create Endpoint and complete the VPC endpoint creation for ECR.
- Leave service categories : AWS services.
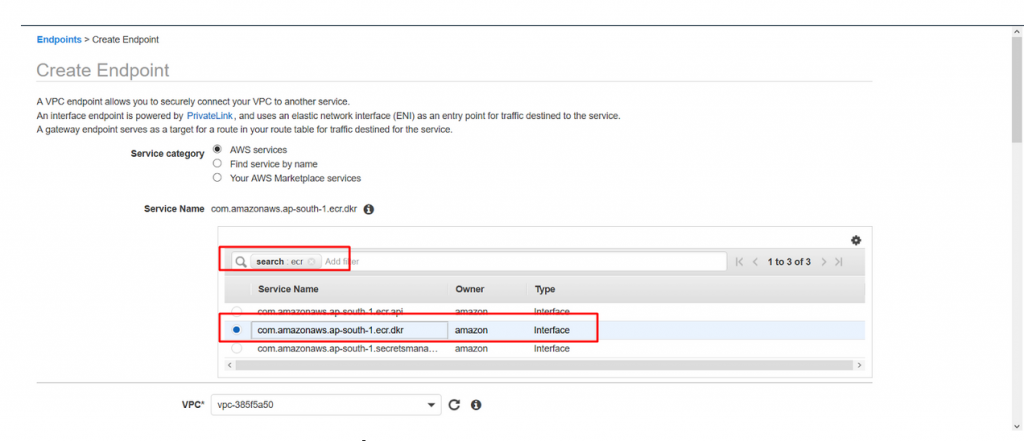
- Service name : Type ecr in search box and hit enter and select the service name as com.amazonaws.ap-south-1.ecr.dkr Please note that the region we are working for is ap-south-1 hence the url has ap-south-1 the URL will be different for your region. Format being com.amazonaws.<region>.ecr.dkr
- UPDATED on 22-09-2022: Amazon ECS tasks hosted on Fargate using Linux platform version
1.4.0requires .api also to be added. Hence please add com.amazonaws.ap-south-1.ecr.api also to End point screenshot below. Please note that the region we are working for is ap-south-1 hence the url has ap-south-1 the URL will be different for your region. Format being com.amazonaws.<region>.ecr.api 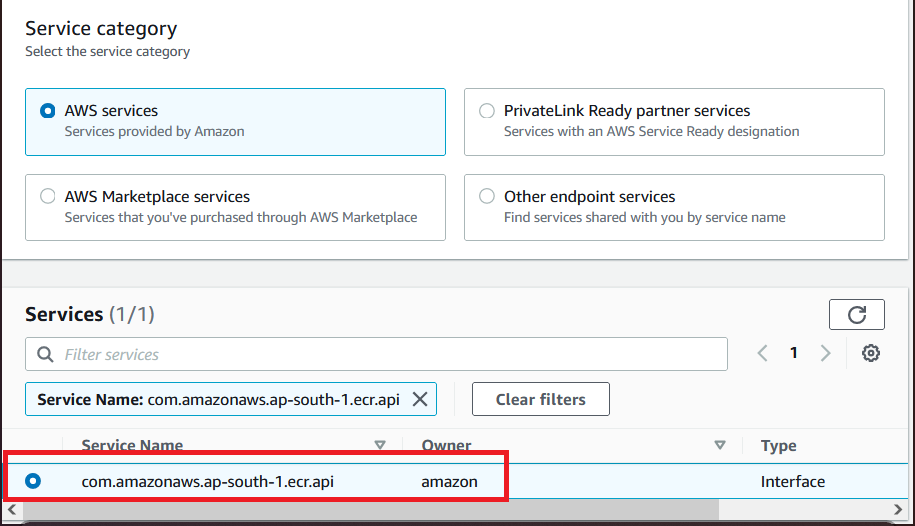
- Leave the VPC as default.
- Leave the subnets as default it will automatically select the subnets form the default VPC.
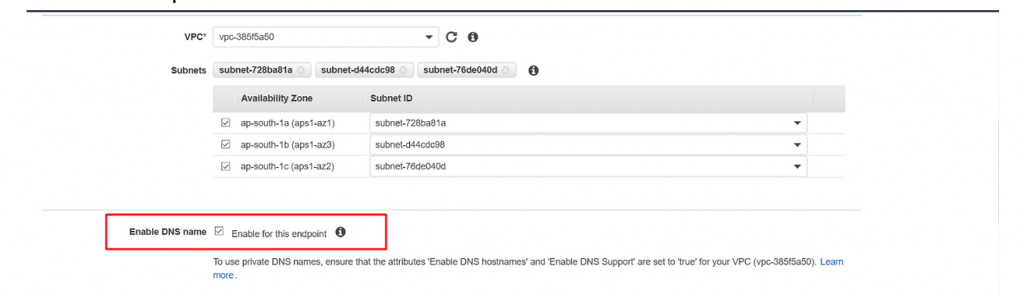
- To use private DNS name make sure Enable DNS name is checked as below.
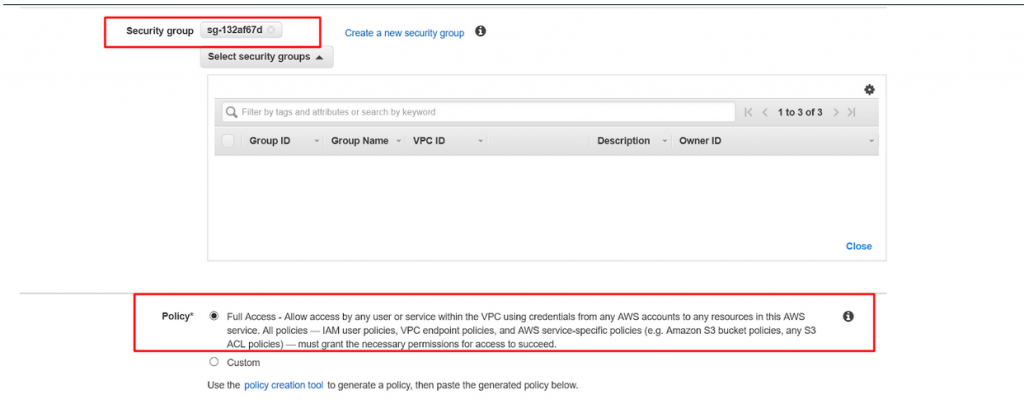
- Leave the security group as default one and policy as full access as below.
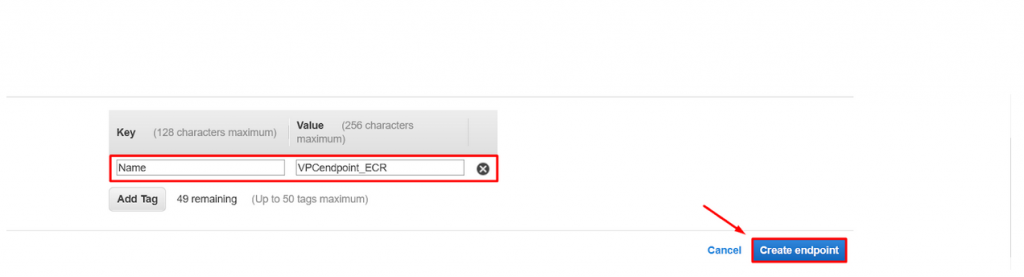
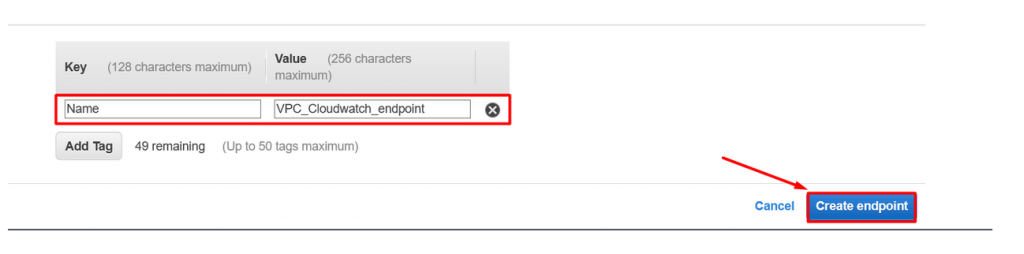
- Click on tag and create name tag for the VPC endpoint and finally click on create endpoint.
- Key : Name
- Value : VPCendpoint_ECR
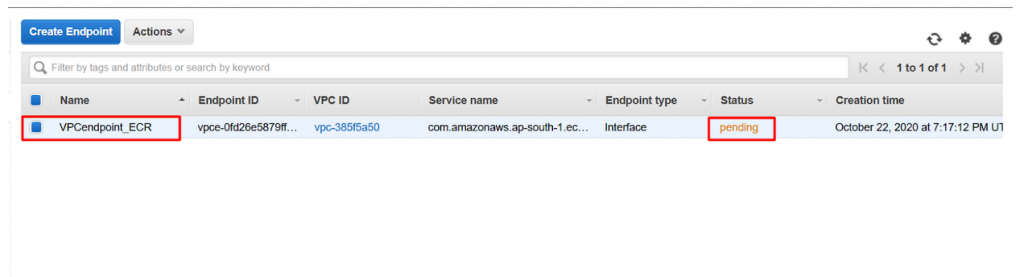
- Now navigate to VPC endpoint and you could see the VPCendpoint_ECR is in pending state.
Add a gateway VPC endpoint for S3
In this step we need to create a gateway VPC endpoint for S3. We are creating it since ECR uses S3 to store Docker images in layers. When we need to pull the images from ECR to build containers, the instances will access ECR to get the image and S3 to download the image.
S3 is using a bit of a different endpoint called a gateway. If we are going to implement s3 gateway for existing applications, then the connections to S3 will be affected while the gateway is being added so we need to be much careful while adding the S3 gateway. When your ECS cluster is using more number of active containers by pulling images through S3 it is recommended to create a new VPC with an S3 gateway, then migrate the ECS cluster and its containers to that newly created VPC.
- Just we need to follow the steps that we followed for creating VPC endpoints for ECR. Navigate to the VPC dashboard and click on Endpoint in the left panel. You could see the VPC endpoint created in above step.
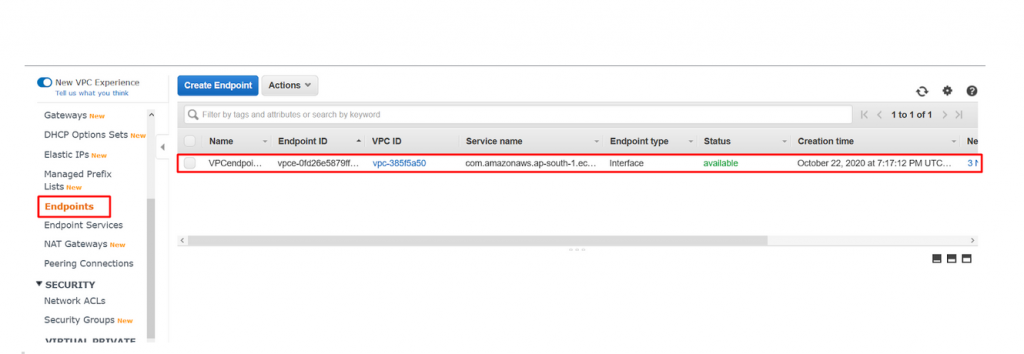
- Click on Create Endpoint to create new one and configure it as below.
- Service Category : Leave it as AWS Services.
- Service name : Type s3 in search box and enter and select as below.
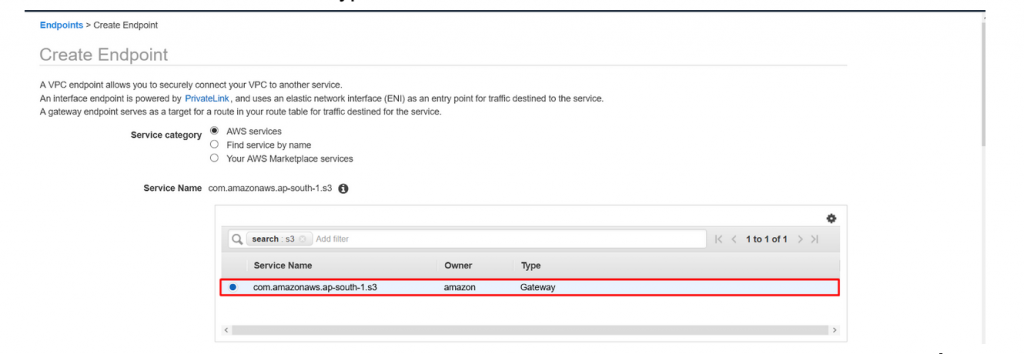
- Scroll down bit and leave the VPC as default and select the default route table for routing via s3 gateway.
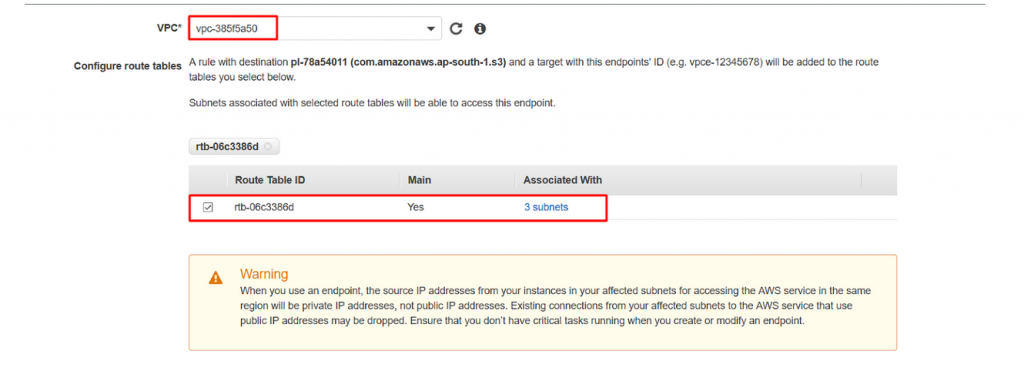
- Now leave the policy as default and give the proper name for your endpoint. Here we have given the name as VPC_S3_endpoint as below and finally click on create endpoint to complete the creation.
- Key : Name
- Value : VPC_S3_endpoint
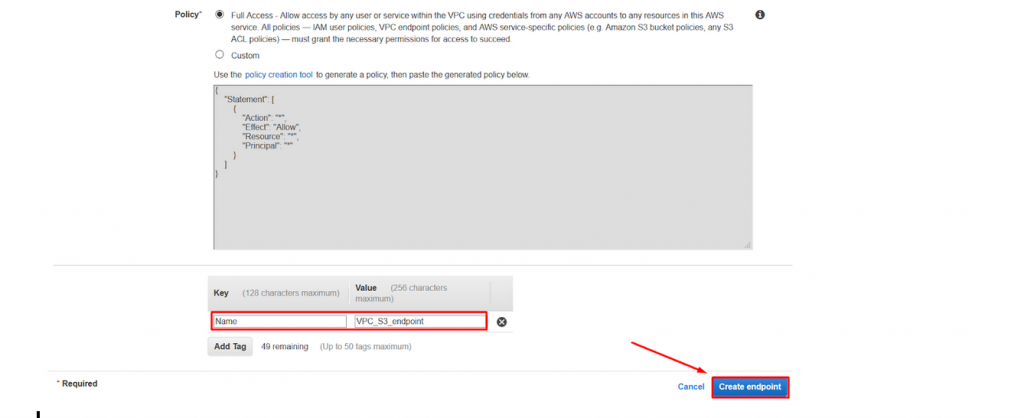
- Navigate to the Endpoint dashboard and you could see the Two Endpoints running as below.
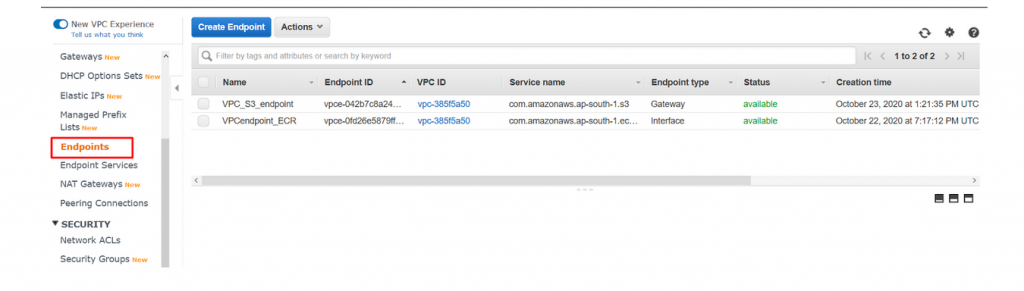
- Now navigate to Routetable dashboard and select the default route table and you could see the new route created for s3 gateway.
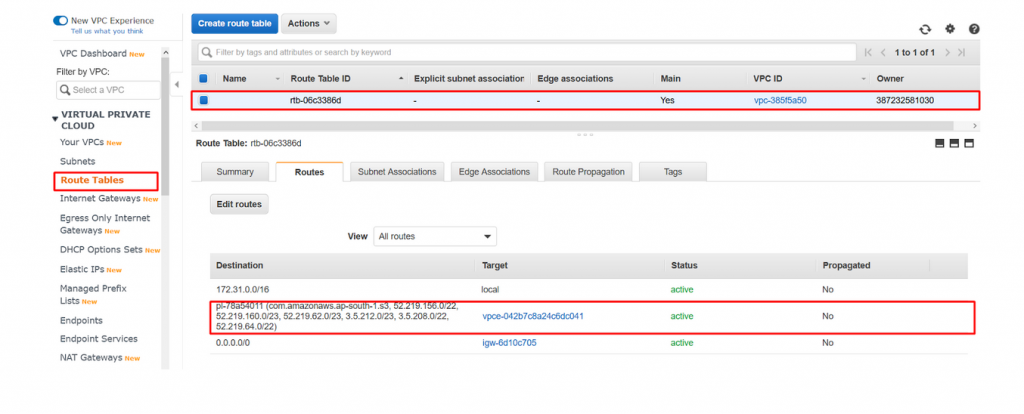
- We have successfully created s3 gateway to pull the images from ECR over private link.
Create the CloudWatch Logs endpoint
Amazon ECS tasks using the Fargate as a launch type will use VPC without an internet gateway and they will use the awslogs log driver to send logs to AWS CloudWatch. To make them send the logs over a private link we need to create an endpoint for logs and you can follow the below steps to create a new one for logs.
- To store the logs for the VPC endpoint we need to create a separate endpoint for a cloudwatch that will send the logs to the cloudwatch.
- Navigate to VPC dashboard → endpoint and to create a new endpoint for logs.
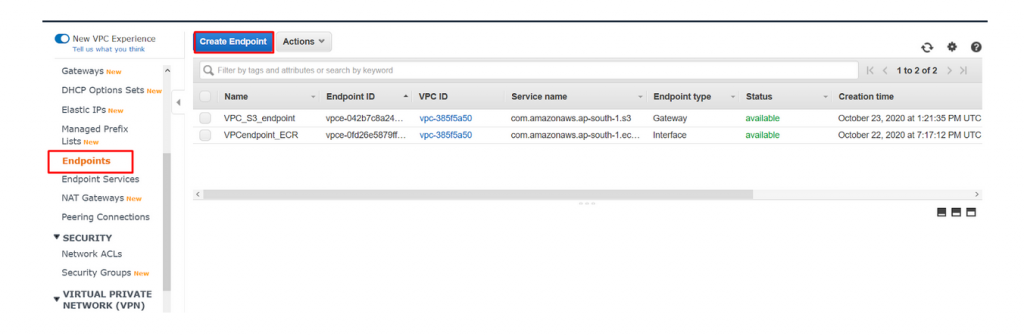
- Now create a new endpoint with following configurations.
- Service category : Leave default as AWS services.
- Service Name : type logs in search bar and hit enter and select as below.
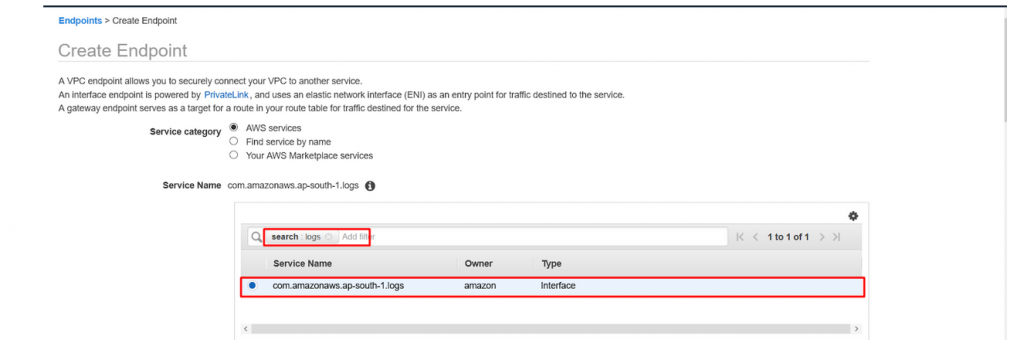
- Scroll down and Leave the VPC field as default, select all the subnets and make sure Enable DNS name is selected.
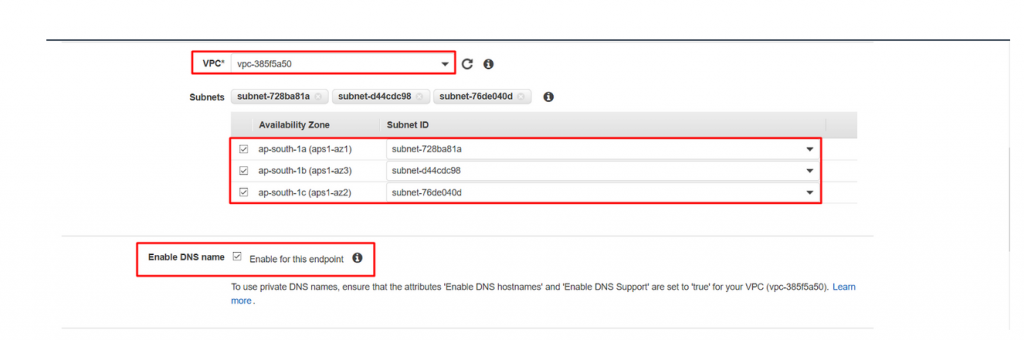
- Now Leave the security group as default and also leave the Policy with default settings.
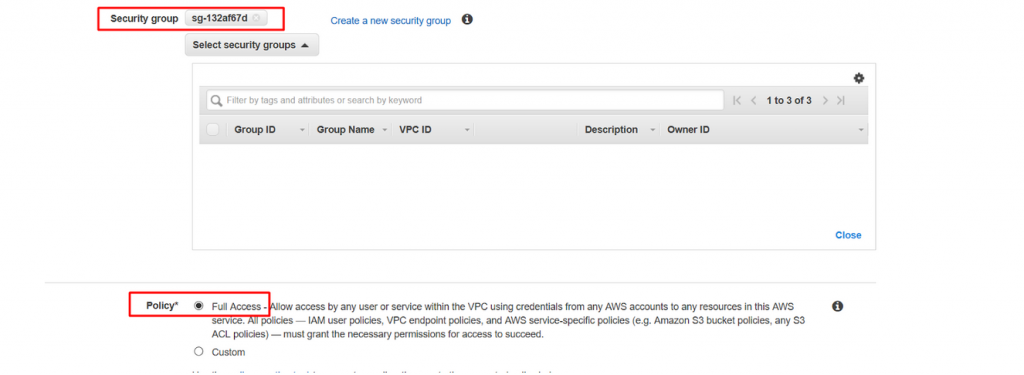
- Now create name tag as below and click on create endpoint to complete the endpoint creation.
- Key : Name
- Value : VPC_Cloudwatch_endpoint
- Navigate endpoint dashboard and you could see the three endpoints are running successfully.
Conclusion
- We have successfully created three VPC endpoints.
- Wait for a week and from the billing dashboard you could see the considerable changes in VPC cost stating that the connections are happening via private link and not via internet.
- Cost after implementing VPC endpoint.
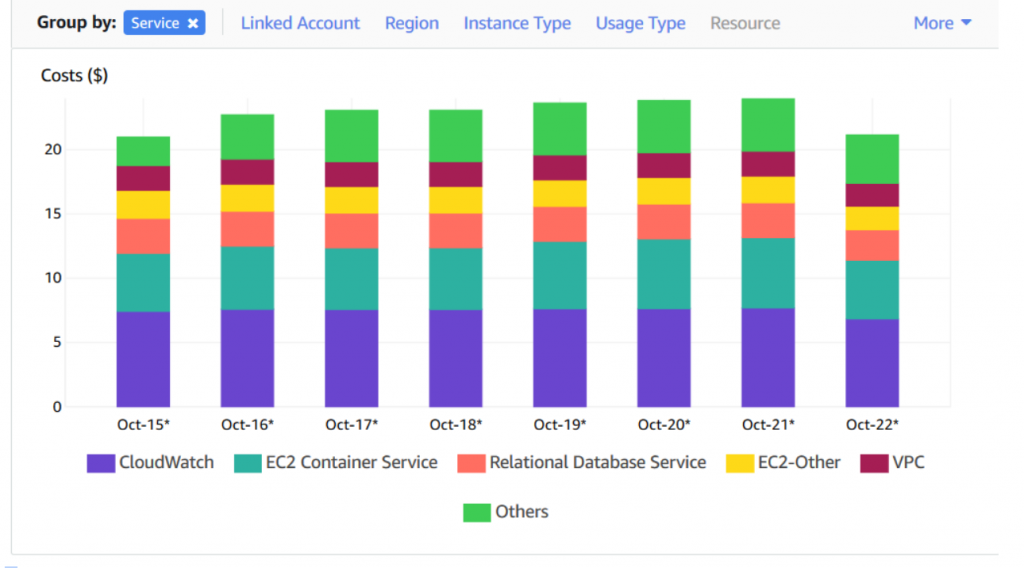
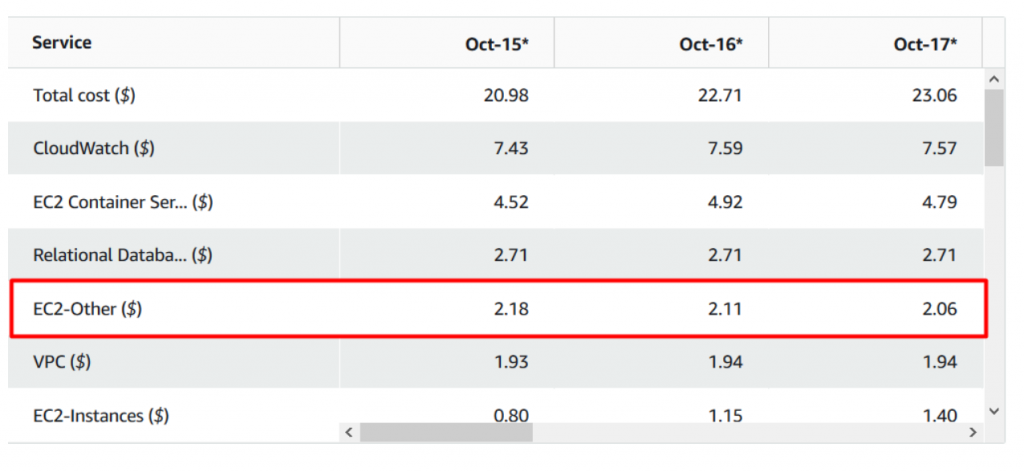
Note:This Is after implementing endpoints. You could find a vast differences in the cost. Thus you saved a lot of AWS bills by using VPN Private Link for ECR.