What are Cloud Security Services?
Cloud security services encompass a wide range of services designed to reduce risk and enhance cloud compliance. The cloud environment is subjected to various threats and risks and integrates a wide range of technologies and processes at the same time. So it’s harder to protect it with a one-stop solution. Instead, many of the cloud services can be able to tackle some areas. Let’s look into them in detail.
These services can be highly managed and controlled by third parties. Also offloading the various security operations to third parties provides the following benefits as follows:
Threat monitoring and detection: Threats and vulnerabilities can be easily identified and responded by the security experts and they will apply suitable remediation to control those risks. This can ensure the safety of the residing data and applications.
No need for manual inspection: The IT staff need not to take care of the security incidents. They can focus on managing and supporting the business operations.
Cloud security service’ best practices
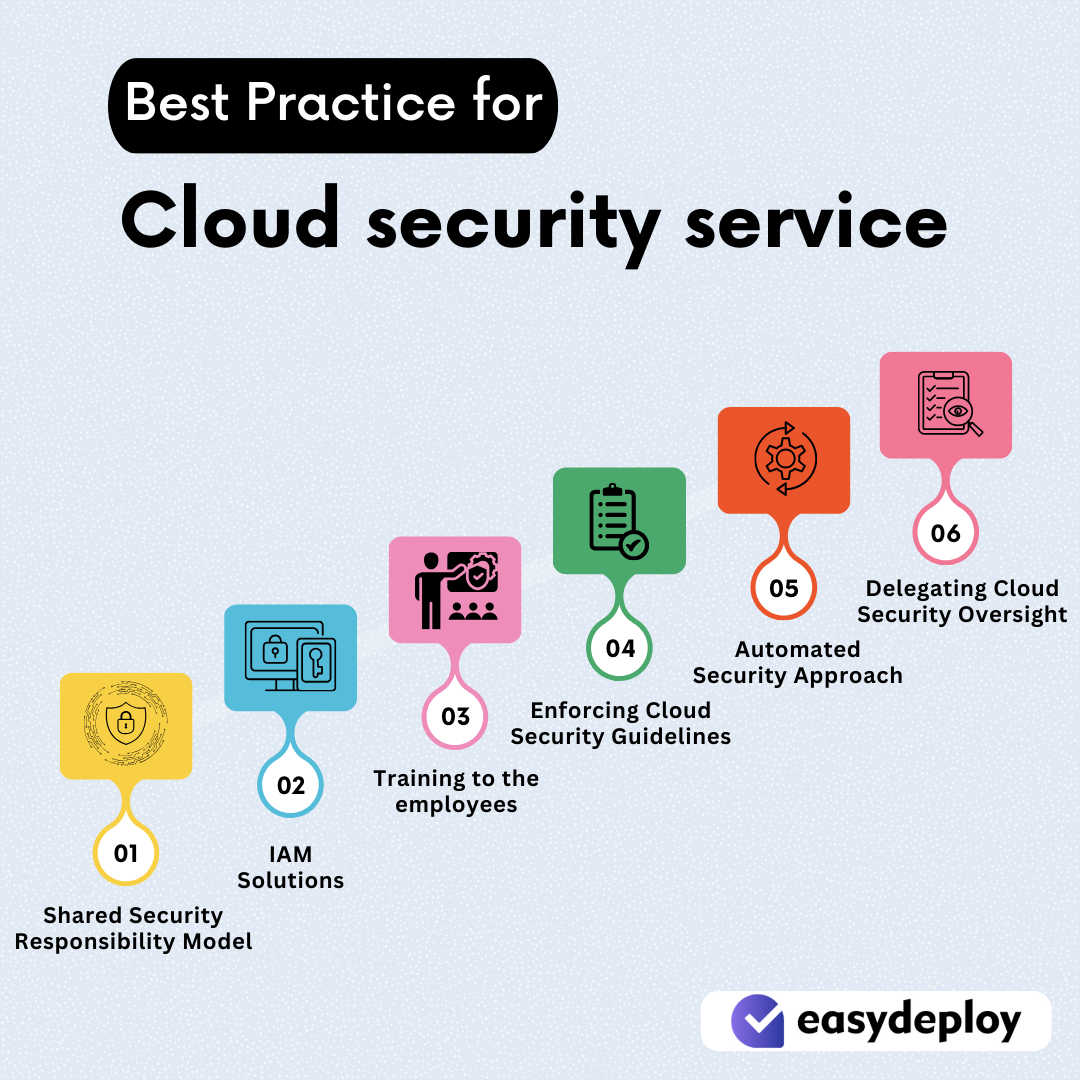
With the availability of a vast number of cloud security service in today’s cloud market, it is tedious to integrate everything into an effective defense layer. To bring efficient security, we need to adhere to some best practices to make use of most of the cloud security service.
Here are some best practices while using the cloud security services:
Shared Security Responsibility Model
Before beginning your journey in the cloud security program, it is essential to understand the role of the shared security responsibility model. It helps to define what cloud areas you are responsible for taking care of and which ones are controlled by the cloud provider. In general, the provider can take care of the cloud security and you are responsible for maintaining the cloud security.
Various cloud service offerings such as SaaS and IaaS need to take care of varied takes on this model to do their daily operations efficiently. The cloud providers must withhold the data of which one is operating better and which one is not.
Identity and Access Management Solution
The data breach report released in 2021 has revealed that the detected cloud misconfiguration is a highly vulnerable attack vector. What’s interesting is? The detected attacks are not intentional. So, the one-stop solution is limited privileged access for those who need the data urgently. Or else, limiting the administrative function’s scope to the specific administrator also can be a better idea.
On the other hand, you should not grant administrative rights to a single person. All this can be made possible with the help of the IAM solution.
Also Read: What are AWS IAM (Identity and Access Management) Roles & Policies? (easydeploy.io)
Training to the employees
As we already know, humans are the greatest threat in the security chain. Something needs to be done to defend those threats. Or else, whatever security initiatives you are taking will be wasted. The best way to overcome this concern is to educate the employees who are dealing with the security areas on how to handle the data and applications and how to encrypt the data while using it.
You must ensure that all the security members in an organization undergo awareness training and keeping updated with the latest threats is of paramount importance. And they must know the impact of threats such as phishing, spear phishing, and other social engineering attacks and they must be ready to apply suitable security solutions.
This kind of training must be incorporated during the onboarding process so that they can be tuned with the right mindset from day one.
Drafting and Enforcing Cloud Security Guidelines
For a seamless rollout of your cloud protection measures, it’s essential to jot down all pertinent rules, methods, and steps. Think of these as guiding lights that everyone in the company should adhere to. But remember, these guidelines should be written and remembered. Leaders should actively promote them, ensuring that every team member understands and embraces them.
Layered Automated Security Approach
Given the increasing complexity of cyber threats, your cloud security setup must be robust and multi-layered. Imagine building a fortress with multiple barriers; others should still stand strong if one falls.
To maximize the efficiency of your defenses, it’s crucial to weave these security tools together, making them automated and in sync. This not only reduces manual tasks but also enhances the overall security posture, making threat identification and response swifter, all while keeping costs in check.
Delegating Cloud Security Oversight
Recognizing that not every company boasts an in-house cybersecurity brigade or a dedicated security hub, the idea of managing intricate cloud defenses can be daunting. If your organization falls into this bracket, the smart move might be to delegate these responsibilities.
Consider collaborating with external entities like managed security service providers (MSSPs). They bring expertise in cloud security management and can shoulder the bulk of your security concerns. This way, you can channel your energies towards what you do best – your business endeavors.
Top benefits of employing cloud security service in your business
The core benefits of applying cloud security service in your business such as:
Cost Efficiency
Traditional data breaches in the cloud can lead to substantial losses, averaging around $3.8 million.
Utilizing cloud security solutions can be a cost-effective approach, eliminating potential financial drains related to cyber incidents. The absence of maintenance overhead makes it a more affordable choice, significantly reducing the financial implications of security breaches.
Flexibility and Scalability
Cloud computing offers adaptability, allowing businesses to access software and storage resources as needed. Coupled with cloud security measures, it ensures that as business demands fluctuate, security provisions can scale up or down accordingly. This flexibility ensures that while businesses evolve and grow, their security posture remains robust.
Protection from DDoS Threats
DDoS attacks pose significant risks to cloud infrastructures. Cloud security mechanisms actively monitor and counteract such threats, safeguarding the integrity of server resources by identifying and neutralizing abnormal traffic patterns.
Cost Savings on Operations
Adopting cloud security solutions often translates to reduced operational and administrative costs. Entrusting security responsibilities to a Cloud Security Provider (CSP) eliminates the need for in-house security personnel, ensuring expert oversight without the associated staffing costs.
Enhanced Reliability and Accessibility
Cloud security ensures uninterrupted access to vital data and applications. With stringent security protocols in place, authorized users can access resources consistently, ensuring immediate responsiveness to potential security challenges.
Robust Disaster Recovery
The cloud stores critical business data, making its protection paramount. Effective cloud security measures ensure that only authorized entities access sensitive data, mitigating risks associated with inadvertent data exposure or human errors.
Compliance with Regulatory Standards
Adherence to data protection regulations like HIPAA and GDPR is imperative for businesses. Cloud security frameworks are designed to align with these regulations, ensuring business integrity and data privacy.
Protecting Reputation and Market Standing
Instances of data exposure can impact a business’s reputation and market credibility. Implementing robust cloud security measures minimizes the risk of unintentional data leaks, preserving the trust and integrity of the organization in the marketplace.
Conclusion
If your organization isn’t fully on the cloud yet, chances are you’ll be shifting some operations there soon. Before you do, it’s important to think about how to keep those operations safe by looking at security and the rules you need to follow.
Before switching to cloud services, consult with cloud security consulting experts on how to safeguard your cloud ecosystem.
We at EasyDeploy assist you in applying the right security strategies to secure your cloud network with the utmost security. Our cloud security consulting experts are available 24/7 and offer the right solutions at the right time.